CrimeStar RMS software provides some basic login security features that validate the user identity and control their access to different modules and features within the system. You must have administrative security access rights to the software in order to make a security authorization changes.
To access the CrimeStar RMS Security Administration form, select ‘System’ from the main menu. Then select ‘Security’ from the ‘System’ menu. You will then be shown the CrimeStar Security Administration Form.

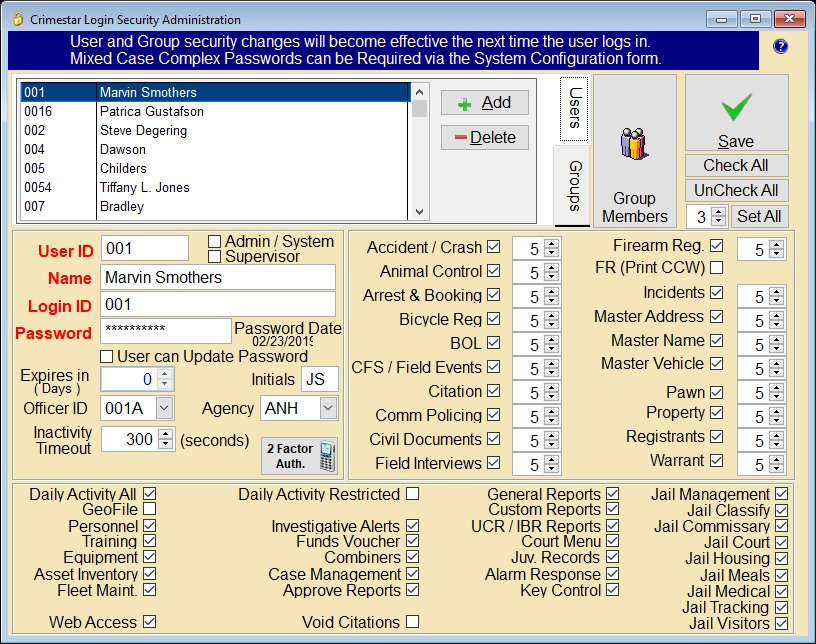
Use the button labeled ‘Add’ to create a new CrimeStar user. Enter values for the following user security fields that re presented on the form. Data fields labeled in RED are required. The table below provides a description of data fields.
User ID: |
A User ID is a 6
character alphanumeric value that uniquely identifies the user
to the system. This value, once set or established for a
user should probably be permanent and not changed. As
new records are input to the system or existing records are updated,
each record is tagged with the User ID for the user making those
changes. The User ID is also recorded in the system audit
logs to indicate user activity. |
Admin /System |
This checkbox determines if the user is designated as a Crimestar RMS system administrator giving them access to the "System" menu and all the program options that the system menu contains.
|
Supervisor |
This
checkbox determines if the user is designated as a supervisor.
Supervisors (and System Administrators) are given access to the
Case Management section of the Crimestar program listed under
the Admin Menu. |
User Name: |
The User Name is
a plain text reference for the common name of the person represented
by the User ID. i.e. "Sgt. John Smith". |
Login ID |
The Login ID is the value that users actually enter on the RMS login form to gain access to the system. This value is deliberately separate from the User ID so that the login ID value for any given user can be changed as needed. A Login ID can be a maximum of 20 characters long. Generally, similar to passwords, the longer the Login ID value the better the security.
* By
default, Login ID's are
not case sensitive. However
Login ID's can, via the Locking & Security system configuration,
be made case sensitive requiring the user to enter his/her Login
ID exactly as it was defined within the system security administration
module. |
Password |
Passwords are ALWAYS case sensitive requiring them to be entered exactly as they were defined. A password can be a maximum of 20 characters long. Generally the longer a password is the more secure it is.
The system does however,allow you to enforce more Complex Password rules requiring that any password defined in the system meet the following Complex Password criteria. When the system is set to require Complex Passwords the following FBI/NCIC compliant password criteria are enforced:
Users are given 3 attempts to successfully login before the software will shutdown. When Complex Passwords are turned on, after 3 failed login attempts using the same Login ID, the user's login account will be temporarily locked for a period of 10 minutes.
** Passwords are ALWAYS stored in the Crimestar database in an encrypted format so that any subsequent examination of raw database tables by IT personnel or transaction audit logs by system users does not reveal any password values.
|
User can Update Password
|
This optional setting allows a user to update their own password via the user menu. |
Expires in (Days) |
In all circumstances (Complex passwords or not) when users are permitted to Update their own password, the system administrator can define the frequency, in days, in which the users defined passwords will expire. Once a password has expired it must be reset by a system administrator.
|
Officer ID |
This setting links the user's security login
with a designated Officer ID as defined in
the OFFICER code
table category of the Systems "Other Codes".
The Officer ID value is a 6 character (max) official published
permanent designation for the Officer within the Agency (sometimes the badge #), used
on all Crimestar documents. Since the security system's
private User ID and Login ID may or may not actually be the same
the officer's official published Officer ID designation, the
Officer ID can be linked to the system security User ID via this
setting. This Officer ID will be used for Crimestar E-Mail and to automatically populate certain other areas of the program such as the Daily Activity Log Toolbar.
|
Initials |
This is a 3 character field to hold the initials of the user's proper name.
|
Inactivity Timeout |
This values determines how long the user can leave a workstation that they are logged into, inactive before the system will automatically logout the user and shutdown the workstation. User's who leave workstation's logged in and unattended allow other potentially unauthorized people to access system data. They also consume a concurrent user license to he software potentially preventing someone else from logging into the system.
* Timeout values are entered in seconds rather than minutes. Therefore a timeout value of 300 is (300 seconds / 60 seconds in a minute = 5) 5 minutes. The maximum timeout values that can be set for both the Initial Login and Inactivity timeout is 999999 seconds, which is approx. 11.5 days. Entering a value of zero "0" instructs the software to not timeout and to wait indefinitely.
|
System Modules & Features |
Once a user is defined, you may activate or deactivate the modules and portions of the program that the user will be allowed to access by checking the appropriate box that represents the module or program function. A checked box represents authorized access and an empty box represents no access. In addition to providing specific users access to certain modules via the security file, make sure that the desired program modules are turned on for system access via the Menu Items page of the system configuration.
Additionally you will want to assign that user an access level for one or more modules or program features. Access Levels range from 0 to 5 with 5 having the highest level of access. These access levels are used in conjunction with the CrimeStar record locking functionality. This process allows a system administrator to ‘Lock’ a record for View, Edit and Delete access. If the users access level is less than the level assigned to the record for view, edit or delete access the user will not be allowed to perform that function.
|
Group Settings |
Security settings may also be created for GROUPS. When users are added to a specific GROUP they automatically inherit all the security rights and authorizations that have been given to that respective group. A single user may be a member of multiple groups. Each user will inherit the highest access level provided by the group(s) that the user belongs to.
|
2 Factor Authentication |
Two Factor Authentication is a great way to add an extra layer of security to your system. Beyond a valid Login ID and Password, the user must also enter a random 6 digit Security Code that is sent specifically to that user's pre-configured e-mail address or cell phone #.
To configure a user for 2 factor authentication, the 2 factor authentication option must be activated within the Security section of the RMS system configuration and either an E-mail (SMTP) and/or a Subscription Message Service (SMPP) host server must be configured. Both SMTP (e-mail) and SMPP (high speed text message) servers can be configured in the Security section of the RMS System Configuration however when both are configured the faster SMPP service is used by default. If neither an SMTP or SMPP host server is configured in the Security section of the RMS System Configuration then the 2 Factor Authentication process is automatically deactivated so as to avoid users from being locked-out of the system.Once activated a button labeled "2
Factor Auth." will appear on the Login Security Administration
form. Select the user you wish to configure for 2 factor
authentication and click the 2 Factor Auth. button to activate
2 Factor Authentication Settings sub-form.
Crimestar software will use your SMTP E-Mail server for the delivery of e-mail or SMS/TXT messages. This e-mail to TXT message service is typically available with all mobile phone carriers. However, the speed of that respective service will vary widely depending upon how busy the service provider's mail queues are and what relative priority the service provider gives SMS messages received via their e-mail gateway.
See Mobile Phone SMS E-Mail Gateways for information regarding sending SMS messages via e-mail.
PRIORITY MESSAGE DELIVERY If the speed and reliability of sending an e-mail to your cell phone carrier e-mail gateway is insufficient for your needs, using Crimestar's high speed paid subscription mobile data messaging service may be a preferred option. The cost for this paid subscription is very reasonable. SMS subscription services can and do offer much faster speeds and higher reliability regarding the delivery of your SMS messages. Since many of these SMS service providers have monthly minimum message requirements that can far exceed the typical usage for a small department, Crimestar has negotiated a master contract with a major SMS service provider. By obtaining your SMS message service thru Crimestar's master contract re-seller agreement you can simplify the implementation of the faster message delivery service, avoid the setp fees and monthly minimum message requirements and still get a very competitive per message rate on SMS message delivery. Contact Crimestar for more information.Cost Estimate: The cost per SMS text message via an SMS service provider using the faster SMPP protocol can vary depending upon your usage volume. For budgeting purposes you should plan on about $0.01 ( a penny ) per message.
Estimating your usage volume requires you to make some educated assumptions:
Consider a small agency that has 3 officers on duty at any given time. Now let's assume that there will be about 10 Two-Factor Authentication SMS Text messages generated per officer per shift. This number will vary depending upon your organization and how frequently you Log-In/Log-off of the Crimestar system. So, we will do the math: ( 3 officers x 10 messages ea. = 30 messages per shift x 3 shifts per day = 90 messages per day x 30 days in a month = an estimated 2,700 messages per month. At $0.01 per message your message cost would be approximately $27 per month. |
To Delete a CrimeStar user, position the record pointer on the record you wish to delete. The record pointer is a small black triangle in the column immediately to the left of the User ID in the list of users. Click the button labeled ‘Delete’ to delete that user.
Security of your Data: For those of you who plan on using the Synchronization utility to have laptops (or any other kind of field computer) out in the patrol car, security of that data can be a major consideration. While access to the Crimestar database is password protected via the Crimestar application software, those with some computer programming skills could still access the data directly from the database without using the Crimestar program software. The (Your Data) data as stored in the Crimestar database is not encrypted. In the event that your laptop or computer were to be stolen out of a patrol car or simply lost, the data contained within the Crimestar database could be at risk of disclosure to unauthorized persons. One method to help protect the data on your computer is to Encrypt the hard disc or drive volume where the Crimestar software and database is installed. Newer editions of Microsoft Windows provide this capability, however this added level of protection is not turned-on by default. You must expressly turn it on and activate it. If the Drive Encryption available via Microsoft Windows is insufficient there are other very good (FREE) encryption programs that can easily be installed on your computer to protect the data from unauthorized prying eyes...