 Law Enforcement Software
Law Enforcement Software
 Law Enforcement Software
Law Enforcement Software
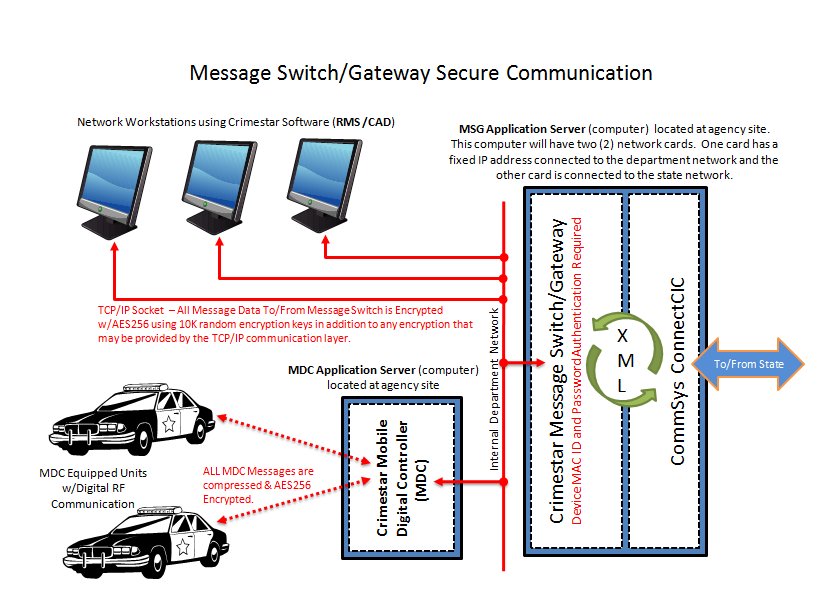
The following diagram illustrates how all communication between client workstation and host controllers are secured by AES256 encryption using a pool of 10,000 encryption keys where each unique message is encrypted using a different encryption key. Where data is exchanged via XML between the Crimestar Message Switch/ Gateway host and the Commsys ConnectCIC application (provided under license by Commsys) both application are typically run on the same physical computer (as shown) which isolates and provide protection of the data exchange.
| See Also : | RMS Entity Diagram |
| E911 Network Communications | |
| MDC Message Process/Flow | |
| MSG Hardware Installation Diagram w/o MDC | |
| MSG Hardware Installation Diagram + MDC |