 Law Enforcement Software
Law Enforcement Software
 Law Enforcement Software
Law Enforcement Software
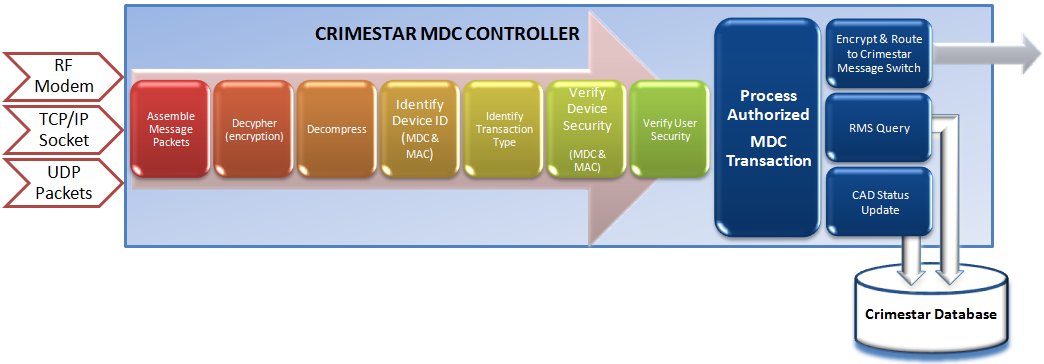
The illustrations below give an over-view of the messaging process used between the MDC workstation and the MDC Controller. They also show, where the MDC Controller passes message transactions to the Crimestar Message Switch Gateway (MSG) product that those messages are also encrypted and an additional layer of device and user verification are performed before any transactions is submitted out to the state/NCIC systems.
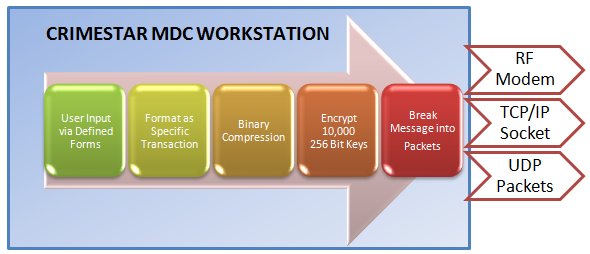
Where Message output from either the MDC Workstation or MDC controller utilizes either the TCP or UDP protocols all messages could be routed thru the tunnel of a Virtual Private Network (VPN) for an additional layer of message security.
The MDC Controller performs device and user security verification on each message processed and performs either CAD or RMS (or Both) inquiries and transactions against the Crimestar Database. In addition to local Crimestar RMS query transactions, if both device and user security authorization exists, query requests can be re-encrypted and forwarded to the Crimestar Message Switch Gateway (MSG) system (Licensed Separately) to submit those respective transactions to State/NCIC systems.
FOR OFFICIAL USE ONLY
| See Also : | RMS Entity Diagram |
| E911 Network Communications | |
| MSG Hardware Installation Diagram w/o MDC | |
| MSG Hardware Installation Diagram + MDC | |
| MSG Secure Communications |