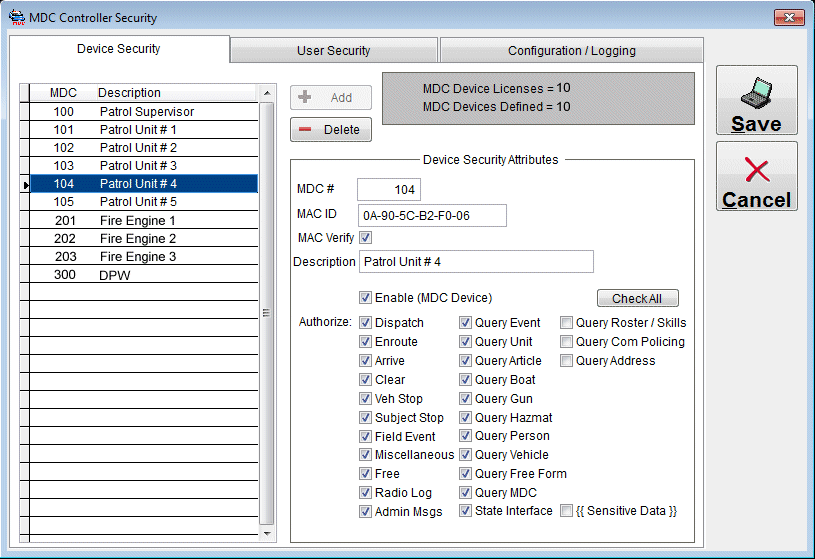
Address Verification: Before any data transactions can be performed from an MDC device the device’s MDC address must configured into the device security table of the MDC controller. All transactions from devices whose MDC address is not configured or authorized are rejected. As part of the MDC address verification process the MDC controller can also optionally verify the computer’s Media Access Control (MAC) ID of the remote MDC device. When MAC ID verification is enabled each MDC submitting transactions must provide both an authorized MDC # and an authorized MAC ID associated with that specific MDC address. Unlike MDC addresses, MAC ID’s are not part of the message header but rather are part of the encrypted data making the unauthorized interception of valid MAC ID’s virtually impossible.
Transaction Type Verification: Once the MDC device (and optionally the device MAC ID) is confirmed as authorized, individual transactions can be submitted. However, individual transaction types can be authorized or de-authorized at the MDC controller on a device by device basis. This allows the same MDC system to be used for various agency types (i.e. Police, Fire, Ambulance, etc.) for dispatch purposes while preventing unauthorized access and maintaining the security of sensitive data local database and State/NCIC data.

The number of MDC devices that can be defined in the Device Security table is restricted to the number of MDC device licenses purchased.